Everybody nowadays very well prefers to work in a remote environment where they will be sharing a good number of files with every passing day. So, having a good understanding of the multiple sources and tools in this particular case is important because some of the activities are perfectly unavoidable and have become a very important concern for businesses to function smoothly. So, being very clear about the technique charities of credentials in this particular case is important, and ultimately people need to have a good understanding of the readability in this case so that things are very well sorted out
What do you mean by a hashing algorithm?
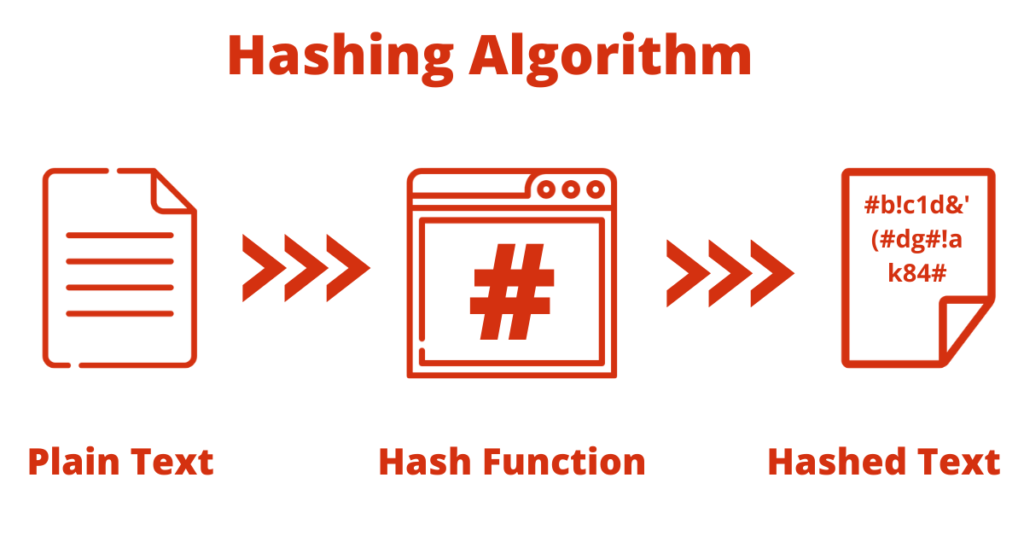
The hashing algorithm is a fundamental component of the cryptography concept and ultimately will be based upon dividing the data into smaller mixed-up pieces which makes it very difficult for the end user to go back to the original value and text. This particular function basically will be the algorithm that will be generating the fixed length result along with specific input data and further this concept is very much different from encryption. Having a good understanding of the security and basic technicalities of the hashing algorithm is very important so that storage of the things will be very well facilitated and there will be no chance of any kind of issues at any point in time.
What are the ideal characteristics to be paid attention to for the best options of hashing algorithm functioning?
- It should always behave as one one-way function: One of the major things that you need to take into consideration at the time of proceeding with the choice of the ideal function is to go for that option which is a perfectly one-way function. In this case, you will be getting the specific result very easily and further, the initial input and other associated things will be more problematic in the whole process
- It is important to understand the avalanche effect: At the time of proceeding with the choice of the best options of the hashing algorithm, understanding the avalanche effect means that input will be providing a particular output but any minor change in the input will be resulting towards significant change in the output has to be understood. So, in this particular case, people need to be clear about the basics of the effect so that things are very well done in the right direction.
- It has to be easy to compute: For any element of a given set of data, input has to be subjected to the options of the hashing algorithm and further getting the results within seconds should not be a problem if the function is built very strongly. So, you should always focus on that particular option which is very fast in terms of computing.
- Functions should be deterministic: The output of one parameter has to be the same irrespective of the number of checks done or every time the user will be using it. This will be especially important at the time of proceeding with the verification of multiple accounts so that things are very well sorted out without any issues in the whole process.
Following are some of the very basic types of hashing algorithms that you need to know for the business world:
- MD5 (MD stands for message direct): This is one of the most commonly used options of hashing algorithm that will help provide people with an extreme level of support. Whenever the past will be converted into a specific pattern with the help of this option, it will become very easy to go for doing the Google search about the value and ultimately have access accessibility to the original value without any problem.
- SHA family of algorithms: This particular point is very important to understand because it was introduced in 1993 and later on has been compromised in significant number of times. SHA-1 is a slightly improved version of this particular system and ultimately has been very well used in the case of SSL securities which also has been subjected to many attacks. SHA-2 is very well recommended to be used by organizations but it is much more complicated. On the other hand, the organization can easily proceed with the choice of SHA-3 which will be based upon a good number of companies who are very serious about security in the whole process.
- Whirlpool: This particular point is a 512-bit HASH function and ultimately provides people with an extreme level of support because it has been undertaken with the help of advanced encryption standards. This point is very important to be understood from the beginning so that everything will be very well done in the right direction and chances of any problem will be perfectly eliminated throughout the process
- RIPEMD family of algorithms: This particular area will be very well standing for RACE integrity primitives evaluation message direct which is vital to be understood by the organizations because it was developed in 1990. Some of the good output length in this particular case will be increasing in the subsequent version and further, the security coverage will also be consistently increasing without any problem in the whole process
- CRC32: This particular point is very important to be paid attention to in the whole process so that things are very well sorted out and everyone will be able to deal with the spreading properties very easily. This particular point is very much quick in terms of providing people with support for the smooth transfer of file with comprehensive validation in the whole process
Hence, being very much clear about the basics of hashing algorithm is definitely need of the hour and ultimately getting in touch with the best experts like Appsealing is important for the companies so that they can go for introducing the perfect options of hashing algorithm very easily. As an organization it is very important for the companies to remain updated with the latest technology in this particular area so that business continuity will be easily enjoyed and credential verification will be perfectly carried out with the help of perfect options of hashing algorithm